(→Automating the login) |
(→Setting up VPN via SSHD) |
||
| Line 29: | Line 29: | ||
First, on zm.home, ensure IP forwarding is enabled via <pre>sysctl net.ipv4.ip_forward</pre>, and set it to enabled in ''/etc/sysctl.config'' if not. | First, on zm.home, ensure IP forwarding is enabled via <pre>sysctl net.ipv4.ip_forward</pre>, and set it to enabled in ''/etc/sysctl.config'' if not. | ||
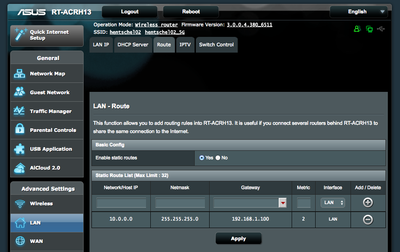
| + | Second, the gateway (default router) on network B needs to be modified to redirect traffic destined for host hentschel via eth0 on host zm.home. We don't redirect all internet traffic via the tunnel, just what is destined for the hentschel host. On the Asus router, that looks like this: | ||
| + | [[File:asus-static-route.png|400px|thumb|left|Under ''LAN''->''Route'']]<br clear=both> | ||
| + | |||
To actually create the tunnel, here is what needs to happen: | To actually create the tunnel, here is what needs to happen: | ||
: on zm.home | : on zm.home | ||
| Line 50: | Line 53: | ||
ip route add 192.168.1.0/24 via 10.0.0.100 | ip route add 192.168.1.0/24 via 10.0.0.100 | ||
</pre> | </pre> | ||
| − | |||
| − | |||
| − | |||
At this point, a request for any host on network B that originates on host hentschel will be answered. At the same time, traffic for hentschel from network B will be directed there via zm.home. Note that the web server on hentschel does '''not''' answer since it's interface is only set to the public interface. | At this point, a request for any host on network B that originates on host hentschel will be answered. At the same time, traffic for hentschel from network B will be directed there via zm.home. Note that the web server on hentschel does '''not''' answer since it's interface is only set to the public interface. | ||
Revision as of 02:45, 24 March 2017
Setting up VPN via SSHD
from this link
- enable
- PermitTunnel yes
- disable
- AllowTcpForwarding yes
Important: Both sides need to run as root to create the tunnel device. Thus, 'ssh -w 0:0 root@www.hentschel.net' must run as root on the client side too.
+---------------+ OpenSSH 4.3 +---------------+
| hentschel | tun0 -- Tunnel Interface -- tun0 | zm.home |
| Has a tunnel | <------------------------------->| Has a tunnel |
| and ethernet | 10.0.0.100 10.0.0.200 | and ethernet |
+-------+-------+ point to point connection +-------+-------+
eth0 | creates a bridge | eth0
198.57.xxx.xxx | that plugs machine B | 192.168.1.100
Routable | into network A |
address | |
here | |
+-------+-------+ +-------+-------+
| Network A | | Network B |
| The Internet | | 192.168.1.1/24|
| Has internet | | Has internet |
| | | NAT gateway |
+---------------+ +---------------+
First, on zm.home, ensure IP forwarding is enabled via sysctl net.ipv4.ip_forward, and set it to enabled in /etc/sysctl.config if not.
Second, the gateway (default router) on network B needs to be modified to redirect traffic destined for host hentschel via eth0 on host zm.home. We don't redirect all internet traffic via the tunnel, just what is destined for the hentschel host. On the Asus router, that looks like this:
To actually create the tunnel, here is what needs to happen:
- on zm.home
- start ssh with -w0:0 (creates tun0 interfaces on both ends), both sides need to be logged in as root
- set tun0 to up
- assign ip address to tun 0
ssh -NTCf -w0:0 root@198.57.xxx.xxx ip link set tun0 up ip addr add 10.0.0.200/24 peer 10.0.0.100 dev tun0 arp -Ds 10.0.0.200 eth0 pub # needed?
- once logged in on hentschel, the following needs to happen on that end
- set tun0 to up
- assign ip address to tun 0
- add route to network B
ip link set tun0 up ip addr add 10.0.0.100/24 peer 10.0.0.200 dev tun0 ip route add 192.168.1.0/24 via 10.0.0.100
At this point, a request for any host on network B that originates on host hentschel will be answered. At the same time, traffic for hentschel from network B will be directed there via zm.home. Note that the web server on hentschel does not answer since it's interface is only set to the public interface.
Automating the login
Here a few tricks at this link
Add the following to ~/.ssh/config (client side):
host targetserver
ControlMaster auto
ControlPath ~/.ssh/cm_sockets/%r@%h:%p
Then this will work:
$ ssh -fNT -Llocalport:remoteserver:remoteport targetserver $ ssh -O check targetserver Master running (pid=23450) $ <do your stuff> $ ssh -O exit targetserver Exit request sent. $ ssh -O check targetserver Control socket connect(/home/sorin/.ssh/cm_socket/sorin@192.0.2.3:22): No such file or directory